Secure your on premises or cloud-based assets whether youre hosted in AWS, Microsoft Azure, or Google Public Cloud. The attacker then uses the rootkit to steal passwords, keys, credentials, and retrieve critical data. The code that is executed against the database must be strong enough to prevent injection attacks. Following are a few security tools commonly deployed by organizations to prevent cyber attacks. The target site is flooded with illegitimate service requests and is forced to deny service to legitimate users. Additionally, SQL injection is very common with PHP and ASP applications due to the prevalence of older functional interfaces. Increase the size of the connection queue and decrease the timeout on open connections. The attackers computer disconnects the client from the server. The NotPetya attack hit targets around the world, with several waves continuing for more than a year, costing more than $10 billion in damage. 
 The malware landscape evolves very quickly, but the most prevalent forms of malware are: Denial-of-service (DoS) attacks overwhelm the target system so it cannot respond to legitimate requests. Fileless malware resides in the devices RAM and typically access native operating system tools, like PowerShell and Windows Management Instrumentation (WMI) to inject malicious code. Unlike attacks that are designed to enable the attacker to gain or increase access, denial-of-service doesnt provide direct benefits for attackers.
The malware landscape evolves very quickly, but the most prevalent forms of malware are: Denial-of-service (DoS) attacks overwhelm the target system so it cannot respond to legitimate requests. Fileless malware resides in the devices RAM and typically access native operating system tools, like PowerShell and Windows Management Instrumentation (WMI) to inject malicious code. Unlike attacks that are designed to enable the attacker to gain or increase access, denial-of-service doesnt provide direct benefits for attackers.  Because 1 = 1 always evaluates to TRUE, the database will return the data for all users instead of just a single user. With so much confidential and personal information being shared online, its not surprising that data breaches have become more common. Phishing attacks occur when a malicious attacker obtains sensitive information from a target and sends a message that appears to be from a trusted and legitimate source. DoS attacks saturate a systems resources with the goal of impeding response to service requests. Bots make up a large percentage of Internet traffic.
Because 1 = 1 always evaluates to TRUE, the database will return the data for all users instead of just a single user. With so much confidential and personal information being shared online, its not surprising that data breaches have become more common. Phishing attacks occur when a malicious attacker obtains sensitive information from a target and sends a message that appears to be from a trusted and legitimate source. DoS attacks saturate a systems resources with the goal of impeding response to service requests. Bots make up a large percentage of Internet traffic.  Ransomware is one of the most prevalent types of attacks, with some attacks using extortion techniques, such as threatening to expose sensitive data if the target fails to pay the ransom. API solutions can help enforce these security controls for APIs in a centralized manner. But a man-in-the-middle attack can be injected into the middle of communications in such a way that encryption will not help for example, attacker A intercepts public key of person P and substitute it with his own public key.
Ransomware is one of the most prevalent types of attacks, with some attacks using extortion techniques, such as threatening to expose sensitive data if the target fails to pay the ransom. API solutions can help enforce these security controls for APIs in a centralized manner. But a man-in-the-middle attack can be injected into the middle of communications in such a way that encryption will not help for example, attacker A intercepts public key of person P and substitute it with his own public key.
Currently, there is no single technology or configuration to prevent all MitM attacks. Once a system has been infected, files are irreversibly encrypted, and the victim must either pay the ransom to unlock the encrypted resources, or use backups to restore them. They can work alone, in collaboration with other attackers, or as part of an organized criminal group. Eavesdropping can be passive or active: Detecting passive eavesdropping attacks is often more important than spotting active ones, since active attacks requires the attacker to gain knowledge of the friendly units by conducting passive eavesdropping before. In the United States alone, the attacks affected nine government agencies and more than 60,000 private businesses. The fraudulent emails often have the appearance of being legitimate, but link the recipient to a malicious file or script designed to grant attackers access to your device to control it or gather recon, install malicious scripts/files, or to extract data such as user information, financial info, and more. This may be inbound traffic, as in a malicious user attempting a code injection attack, or outbound traffic, as in malware deployed on a local server communicating with a command and control (C&C) center. Dozens of well-known accounts were hacked, including Barack Obama, Jeff Bezos, and Elon Musk. Malicious actors often look for ransom or other kinds of economic gain, but attacks can be perpetrated with an array of motives, including political activism purposes. Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks, Buyers Guide for Privileged Access Management, Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks, Ransomware Protection Using FSRM and PowerShell, 4 Steps You Should Take If You Have Been Hacked, [Infographics] Cybercrime In Numbers: How To Protect Your Organization, Active Directory Certificate Services: Risky Settings and How to Remediate Them. Imperva prevented 10,000 attacks in the first 4 hours of Black Friday weekend with no latency to our online customers., Analyze user behavior and data access patterns, Ensure consistent application availability, Secure business continuity in the event of an outage, Imperva Product and Service Certifications, Runtime Application Self-Protection (RASP), Application Security Testing: 3 Types and 4 Security Solutions, Dynamic Application Security Testing (DAST): Ultimate Guide [2022], Top 5 Challenges of Microservices Security, XSS Attack: 3 Real Life Attacks and Code Examples, The Ultimate Beginners Guide to XSS Vulnerability, Natural Language Processing and Mindful AI Drive More Sophisticated Bad Bot Attacks, Imperva Customers are protected from Atlassian Confluence CVE-2022-26134, The 3 Biggest DDoS Attacks Imperva Has Mitigated, Hacktivists Expanding DDoS Attacks as Part of International Cyber Warfare Strategy, Bad Bots and the Commoditization of Online Fraud, 3 Recommendations to Ensure Your API Security Solution can Drive Data Visibility and Quality, Evasive Bots Drive Online Fraud 2022 Imperva Bad Bot Report, Forrester Report Reveals the 5 Benefits IT Teams Really Need from API Security Tools, SQL (Structured query language) Injection. This attack method uses ICMP echo requests targeted at broadcast IP addresses. Threat intelligence databases contain structured information, gathered from a variety of sources, about threat actors, attack tactics, techniques, and procedures, and known vulnerabilities in computing systems. In a world where MSPs use one of many Remote Monitoring and Management (RMM) solutions, its important to know what to look for in a solution that best suits your evolving needs.  A DDoS attack is also an attack on systems resources, but it is launched from a large number of other host machines that are infected by malicious software controlled by the attacker. Hear from those who trust us for comprehensive digital security. One common example is session hijacking, which Ill describe later. So, how can you make sure that Ps public key belongs to P and not to A? Man-in-the-Middle (MitM) attacks are breaches that allow attackers to intercept the data transmitted between networks, computers or users. It occurs when a malefactor executes a SQL query to the database via the input data from the client to server. Drive-by downloads can happen when visiting a website or viewing an email message or a pop-up window. In this attack, an attacker exploits the use of the buffer space during a Transmission Control Protocol (TCP) session initialization handshake. However, first-party cloud security tools are limited, and there is no guarantee that they are being used properly and all cloud resources are really secured. As part of a phishing message, attackers typically send links to malicious websites, prompt the user to download malicious software, or request sensitive information directly through email, text messaging systems or social media platforms. DoS attacks work by flooding systems, servers, and/or networks with traffic to overload resources and bandwidth. Imperva provides security solutions that protect organizations against all common cyber attacks. In addition to implementing good cybersecurity practices, your organization should exercise secure coding practices, keep systems and security software up to date, leverage firewalls and threat management tools and solutions, install antivirus software across systems, control access and user privileges, backup systems often, and proactively watch for breached systems with a managed detection and response service. This process is repeatable, and can be automated to generate huge amounts of network congestion. Advanced Bot Protection Prevent business logic attacks from all access points websites, mobile apps and APIs. Since rootkits hide in legitimate software, once you allow the program to make changes in your OS, the rootkit installs itself in the system (host, computer, server, etc.) SQL commands are inserted into data-plane input (for example, instead of the login or password) in order to run predefined SQL commands. It could also be a link to an illegitimate website that can trick you into downloading malware or handing over your personal information. The last method mentioned is executed in a systematic manner known as a brute-force attack. A brute-force attack employs a program to try all the possible variants and combinations of information to guess the password. Spear phishing is a very targeted type of phishing activity. A replay attack occurs when an attacker intercepts and saves old messages and then tries to send them later, impersonating one of the participants. There are a few countermeasures to a TCP SYN flood attack: This attack causes the length and fragmentation offset fields in sequential Internet Protocol (IP) packets to overlap one another on the attacked host; the attacked system attempts to reconstruct packets during the process but fails. Equifax experienced an open source vulnerability in an unpatched software component, which leaked the personal information of 145 million people. IP packets of this size are not allowed, so attacker fragments the IP packet. Bots can be used for DDoS, to scrape content from websites, automatically perform web application attacks, spread spam and malware, and more. Client-Side Protection Gain visibility and control over third-party JavaScript code to reduce the risk of supply chain fraud, prevent data breaches, and client-side attacks. Some attacks are part of cyberwarfare operations conducted by nation states against their opponents, or operating as part of known terrorist groups.
A DDoS attack is also an attack on systems resources, but it is launched from a large number of other host machines that are infected by malicious software controlled by the attacker. Hear from those who trust us for comprehensive digital security. One common example is session hijacking, which Ill describe later. So, how can you make sure that Ps public key belongs to P and not to A? Man-in-the-Middle (MitM) attacks are breaches that allow attackers to intercept the data transmitted between networks, computers or users. It occurs when a malefactor executes a SQL query to the database via the input data from the client to server. Drive-by downloads can happen when visiting a website or viewing an email message or a pop-up window. In this attack, an attacker exploits the use of the buffer space during a Transmission Control Protocol (TCP) session initialization handshake. However, first-party cloud security tools are limited, and there is no guarantee that they are being used properly and all cloud resources are really secured. As part of a phishing message, attackers typically send links to malicious websites, prompt the user to download malicious software, or request sensitive information directly through email, text messaging systems or social media platforms. DoS attacks work by flooding systems, servers, and/or networks with traffic to overload resources and bandwidth. Imperva provides security solutions that protect organizations against all common cyber attacks. In addition to implementing good cybersecurity practices, your organization should exercise secure coding practices, keep systems and security software up to date, leverage firewalls and threat management tools and solutions, install antivirus software across systems, control access and user privileges, backup systems often, and proactively watch for breached systems with a managed detection and response service. This process is repeatable, and can be automated to generate huge amounts of network congestion. Advanced Bot Protection Prevent business logic attacks from all access points websites, mobile apps and APIs. Since rootkits hide in legitimate software, once you allow the program to make changes in your OS, the rootkit installs itself in the system (host, computer, server, etc.) SQL commands are inserted into data-plane input (for example, instead of the login or password) in order to run predefined SQL commands. It could also be a link to an illegitimate website that can trick you into downloading malware or handing over your personal information. The last method mentioned is executed in a systematic manner known as a brute-force attack. A brute-force attack employs a program to try all the possible variants and combinations of information to guess the password. Spear phishing is a very targeted type of phishing activity. A replay attack occurs when an attacker intercepts and saves old messages and then tries to send them later, impersonating one of the participants. There are a few countermeasures to a TCP SYN flood attack: This attack causes the length and fragmentation offset fields in sequential Internet Protocol (IP) packets to overlap one another on the attacked host; the attacked system attempts to reconstruct packets during the process but fails. Equifax experienced an open source vulnerability in an unpatched software component, which leaked the personal information of 145 million people. IP packets of this size are not allowed, so attacker fragments the IP packet. Bots can be used for DDoS, to scrape content from websites, automatically perform web application attacks, spread spam and malware, and more. Client-Side Protection Gain visibility and control over third-party JavaScript code to reduce the risk of supply chain fraud, prevent data breaches, and client-side attacks. Some attacks are part of cyberwarfare operations conducted by nation states against their opponents, or operating as part of known terrorist groups.
![]() Account lockout best practices and two-factor authentication are very useful at preventing a password attack. Integrate with any database to gain instant visibility, implement universal policies, and speed time to value. It does this using dedicated network equipment, deployed on-premises by the organization, or as a cloud-based service. Firewalls and network security solutions can help protect against small-scale DoS attacks. These vulnerabilities enable attackers to forge untrusted URLs, use them to access an Exchange Server system, and provide a direct server-side storage path for malware. These bots or zombie systems are used to carry out attacks against the target systems, often overwhelming the target systems bandwidth and processing capabilities. Botnets are the millions of systems infected with malware under hacker control in order to carry out DDoS attacks. P2 sends the encrypted symmetric key to P. P2 computes a hash function of the message and digitally signs it. Malware can be used for a range of objectives from stealing information, to defacing or altering web content, to damaging a computing system permanently. Certificate authorities and hash functions were created to solve this problem. Birthday attacks are made against hash algorithms that are used to verify the integrity of a message, software or digital signature. Another common method is the dictionary attack, when the attacker uses a list of common passwords to attempt to gain access to a users computer and network.
Account lockout best practices and two-factor authentication are very useful at preventing a password attack. Integrate with any database to gain instant visibility, implement universal policies, and speed time to value. It does this using dedicated network equipment, deployed on-premises by the organization, or as a cloud-based service. Firewalls and network security solutions can help protect against small-scale DoS attacks. These vulnerabilities enable attackers to forge untrusted URLs, use them to access an Exchange Server system, and provide a direct server-side storage path for malware. These bots or zombie systems are used to carry out attacks against the target systems, often overwhelming the target systems bandwidth and processing capabilities. Botnets are the millions of systems infected with malware under hacker control in order to carry out DDoS attacks. P2 sends the encrypted symmetric key to P. P2 computes a hash function of the message and digitally signs it. Malware can be used for a range of objectives from stealing information, to defacing or altering web content, to damaging a computing system permanently. Certificate authorities and hash functions were created to solve this problem. Birthday attacks are made against hash algorithms that are used to verify the integrity of a message, software or digital signature. Another common method is the dictionary attack, when the attacker uses a list of common passwords to attempt to gain access to a users computer and network. 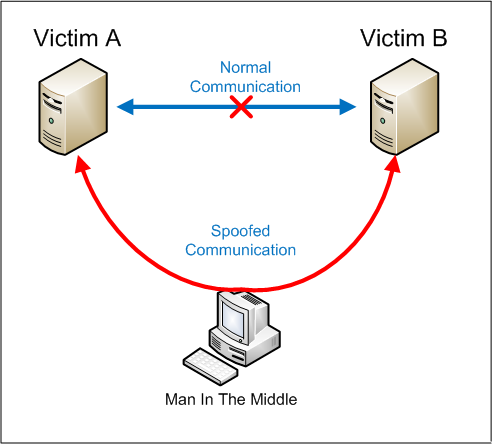
 A trusted application on a privileged system can carry out system operations on multiple endpoints, making them ideal targets for fileless malware attacks. In addition, A could also modify the message before resending it to P. As you can see, P is using encryption and thinks that his information is protected but it is not, because of the MitM attack. Top 10 Cyber Attack Maps and How They Can Help You. P2 creates a symmetric key and encrypts it with Ps public key.
A trusted application on a privileged system can carry out system operations on multiple endpoints, making them ideal targets for fileless malware attacks. In addition, A could also modify the message before resending it to P. As you can see, P is using encryption and thinks that his information is protected but it is not, because of the MitM attack. Top 10 Cyber Attack Maps and How They Can Help You. P2 creates a symmetric key and encrypts it with Ps public key. 
- Alpinestars Venture Xt Pants
- Best Light Brown Hair Dye For Dark Hair
- Lowe's Worx Trimmer Line
- Jelly Belly Sour Hearts
- Jersey Knit Christmas Pajamas
- Multiple Name Necklace Real Gold
- Maternity Tank Tops Plus Size


