Trustwave SpiderLabs reportedon this activity soon after hostilities broke out. However, the general opinion about Stormous is that it is a scam. The community questions whether or not the group has truly breached the companies named and exfiltrated data or if its merely scavenging previously stolen or public information. , with the Stormous group making it seem like they did it. The group has targeted several Indian organizations in the past including: At the time of writing this report, CloudSEK researchers discovered that the threat group is plotting to attack five more organizations, and has hosted a poll for their subscribers, to vote and choose their next target.
If the data leaks expose Personally Identifiable Information (PII), it could enable threat actors to orchestrate social engineering schemes, phishing attacks, and identity theft. Screenshot from the Stormous Dark Web page. ransomware thanatos labs heal security quick analysis encryption demands aes technique across come )html, http://besthost(.)co(.)in/indexSTM(. ransomware msrblog We start the new year with a reported attack on Portuguese media group, The ransomware group Ragnar Locker spread claims of a successful hack of telecom analytics firm, UK based contractor payroll service provider, In the next reported incident Belarusian activists launched a ransomware attack on, South Africa based investment administration provider, Indias only state-owned and operated container terminal, Russian cybercriminal gang Snatch claimed to have stolen 500 gigabytes of data from, The South African division of US-based consumer credit bureau, Lapus$ strikes again, this time San Francisco tech company, The Anonymous hacker group posted on Twitter that they had launched an attack on the, Following a ransomware attack, listed law firm, Relatively new ransomware gang Stormous made headlines when they claimed an attack on, We start the month in Germany where library service, Next up, another library system, but this time in New York. This again brings to mind the possibility of a scam. The technical storage or access is strictly necessary for the legitimate purpose of enabling the use of a specific service explicitly requested by the subscriber or user, or for the sole purpose of carrying out the transmission of a communication over an electronic communications network. The group has recently proclaimed support for Russia in its war with Ukraine, attacking the Ukraine Ministry of Foreign Affairs and allegedly obtaining and making public phone numbers, email addresses, and national identity cards. Request an easy and customized demo for free. Officials at the, The LockBit gang, thought to have strong ties with Russia, announced that they would be releasing files they stole from the, Health-systems and medication-management-solutions provider, Up next is Canadian fighter jet training company, The LockBit ransomware gang claimed an attack on, A ransomware attack in Central New Jerseys, On the last day of the month all computer systems on the network of Costa Ricas public health service ( known as the, We start the month in Australia where the liquidators for building company, Up next was a Memorial Day weekend ransomware attack on the, Back to Italy where this time the BlackCat ransomware gang held the, The RansomHouse ransomware gang claimed an attack on, Officials in Kansas City confirmed that a ransomware attack had affected the, The Hive gang struck again, this time at Pennsylvania-headquartered firm, Japanese automotive component manufacturer. First Floppy is a rental goods and services company based in Delhi. This goal shifted in 2022, adding Ukraine and India to its target list. )html, http://macnnareladelhi(.)com/indexSTM(.
SOCRadar analysts think the group is trying to make a name for itself by using the agenda of groups like Conti.  locky ransomware ransom Some researchers have suggested that many of their attacks are either a scam or the group is exaggerating their claims. Discuss your way into our Community about these threats and stay Vigilant and informed. Our cyberthreat prevention software prevents ransomware, spyware, malware, phishing, unauthorized data collection and profiling and mitigates the risks associated with data breaches and insider threats. They added that they would continue to leak data about company employees, not users personal information. 1712 Pioneer Ave, We share with you some information obtained by SOCRadar analysts by monitoring the dark web.
locky ransomware ransom Some researchers have suggested that many of their attacks are either a scam or the group is exaggerating their claims. Discuss your way into our Community about these threats and stay Vigilant and informed. Our cyberthreat prevention software prevents ransomware, spyware, malware, phishing, unauthorized data collection and profiling and mitigates the risks associated with data breaches and insider threats. They added that they would continue to leak data about company employees, not users personal information. 1712 Pioneer Ave, We share with you some information obtained by SOCRadar analysts by monitoring the dark web.  The cyberattack also had a knock on effect at a county jail when the security camera and automatic doors were knocked offline leaving the inmates in lockdown. The technical storage or access that is used exclusively for statistical purposes. ", He also told Dark Reading, "It is also realistically possible that Stormous may be involved in 'scavenger operations,' which indicates a cybercriminal actor attempting to extort companies whose data had been breached by another threat actor in a previous attack.". )html, http://allahabadnidhi(.)in/indexSTM(. Copyright 2022 Informa PLC Informa UK Limited is a company registered in England and Wales with company number 1072954 whose registered office is 5 Howick Place, London, SW1P 1WG. Join Kurt Baumgartner and Maher Yamout, leading researchers from Kasperskys Global Research and Analysis Team, as they share their perspective on Stormous, including their unique claims, capabilities and motivations.
The cyberattack also had a knock on effect at a county jail when the security camera and automatic doors were knocked offline leaving the inmates in lockdown. The technical storage or access that is used exclusively for statistical purposes. ", He also told Dark Reading, "It is also realistically possible that Stormous may be involved in 'scavenger operations,' which indicates a cybercriminal actor attempting to extort companies whose data had been breached by another threat actor in a previous attack.". )html, http://allahabadnidhi(.)in/indexSTM(. Copyright 2022 Informa PLC Informa UK Limited is a company registered in England and Wales with company number 1072954 whose registered office is 5 Howick Place, London, SW1P 1WG. Join Kurt Baumgartner and Maher Yamout, leading researchers from Kasperskys Global Research and Analysis Team, as they share their perspective on Stormous, including their unique claims, capabilities and motivations.  The threat actor claimed that they discovered a vulnerability in the companys internal network and stole nearly 200 gigabytes of data, including the information of 33 million users. ransomware outbreak Does the Killnet Pose a Serious Threat to Our Industry?
The threat actor claimed that they discovered a vulnerability in the companys internal network and stole nearly 200 gigabytes of data, including the information of 33 million users. ransomware outbreak Does the Killnet Pose a Serious Threat to Our Industry?
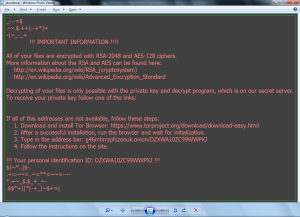 There was an error when registering. Without a subpoena, voluntary compliance on the part of your Internet Service Provider, or additional records from a third party, information stored or retrieved for this purpose alone cannot usually be used to identify you.
There was an error when registering. Without a subpoena, voluntary compliance on the part of your Internet Service Provider, or additional records from a third party, information stored or retrieved for this purpose alone cannot usually be used to identify you.
ransomware strains connections The threat group conducts routine polls on their Telegram channel for subscribers, speculating on who their next target should be. Since 11 April 2022, Stormous ransomware group has been actively targeting Indian entities. The Stormous group has also signaled that it wont stand by and allow other entities, such as ransomware groups, to attack Russia. Sign up to receive the latest security news and trends from Trustwave. Eradicate cyberthreats with world-class intel and expertise, Expand your teams capabilities and strengthen your security posture, Tap into our global team of tenured cybersecurity specialists, Subscription- or project-based testing, delivered by global experts, Get ahead of database risk, protect data and exceed compliance requirements, Catch email threats others miss and prevent data loss, Researchers, ethical hackers and responders, Unprecedented security visibility and control, Key alliances who align and support our ecosystem of security offerings, Join forces with Trustwave to protect against the most advance cybersecurity threats, There is some debate within the cybersecurity community on the validity of Stormous claims, Cyber Attackers Leverage Russia-Ukraine Conflict in Multiple Spam Campaigns, Dark Web Insights: Evolving Cyber Tactics Aim to Impact the Russia-Ukraine Conflict, Dark Web Recon: Cybercriminals Fear More Law Enforcement Action in the Wake of the REvil Takedown. Stormous official statement on its support for Russia. Reset compromised user login credentials and implement a strong password policy for all user accounts. There are some recorded attacks so far, but it should be noted that these are dubious. app_id="6013171b60be8f001cb27363";distribution_key="dist_14"; In 2016,Black Kite began its journey to redefine third-party risk management (TPRM), building the worlds first security ratings service designed from a hackers perspective. Since the Russia-Ukraine war started on Feb. 14, threat groups have been lining up to support each side. London WC2A 2JR The Conti gang was also busy this month with notable attacks on industrial giant Parker Hannifin and Snap On Tools. Keep up with the latest cybersecurity threats, newly-discovered vulnerabilities, data breach information, and emerging trends. The systematic and continuous collection analysis and reporting of changes or trends in the cyber environment, The Persian Pasdaran - Iranian Cyber News and Activities. See our platform Terms and Privacy Policy. ransomware cerber The technical storage or access is necessary for the legitimate purpose of storing preferences that are not requested by the subscriber or user. BlackFog Inc.
However, the general opinion about Stormous is that it is a scam. The Stormous attackers could be simply compiling this already stolen data and packaging it as a new breach in an attempt to earn quick money. The leaked data allows threat actors to gain unauthorized access to personal, proprietary, and Intellectual Property (IP) data. Finally, Stormous claimed to obtain 200GB of data belonging to Epic Games. Monitor for anomalies, in user accounts and systems, that could be indicators of possible takeovers. The Stormous group claims to target western countries and companies. Get access to immediate incident response assistance. ransomware november epidemic analysis decryption tool However, the group did not define the type or amount of data it had taken, and neither Mattel nor Danaher reported suffering a related cyber incident. There is little chatter on the Telegram channel, with the conversation mainly comprised of the groups proclamations. Multiple sources have used Facebook and other social media outlets to try and gather a force to conduct these attacks. The threat actor claimed that they discovered a vulnerability in the companys internal network and stole nearly 200 gigabytes of data, including the information of 33 million users. The operators have shared the data on their website. All rights reserved Cybersecurity Ventures 2018. United Kingdom. Where to find reporting on APTs and hacktivistm. The group's motivating principles and behavior somewhat resemble theLapsus$ hacker group, which targets entities mainly in the Western hemisphere. Discussions began to revolve around some of these attacks being carried out by other threat actors, with the Stormous group making it seem like they did it. The Russian-speaking ransomware group Stormous is claiming to have stolen161GB of data fromCoca-Cola -- and it'soffering to sellthe supposedcache for 1.65 Bitcoin (about $64,000). But the group also claims to have a successful ransomware operation and has taken responsibility for cyber attacks on major American brands Coca-Cola, Mattel and Danaher. From Stormous description, it doesnt seem like the most valuable trade secrets are in the dump file (or that Stormous cant tell if they are there)., Bambeneck added, Whats important for any organization in this kind of position is to rapidly assess what information was taken and what its value is to inform decision makers in situations like this where days of analysis just arent in the cards.. Stormous has also claimed to have successfully attacked several targets in India and Saudi Arabia and possibly a Chinese government site. CloudSEK researchers have noticed that the organizations that the Stormous group claims to have compromised, have been targeted by other groups in the past. PHOTO: Cybercrime Magazine. Hence, the reliability of their claims cannot be verified. Finally, by taking a political stance, it likely hopes to attract supporters with similar viewpoints. )html, http://sigssitamarhi(.)com/indexSTM(. Who Is Stormous and Where Does Its Allegiance Lie? Some of their recent victims include: Additionally, Stormous ransomware group has released a list of Indian domains that could be their potential targets: http://universalkids(.)co(.)in/indexSTM(. Moreover, two of the group's members that were arrested were from mid-eastern countries. Consenting to these technologies will allow us to process data such as browsing behavior or unique IDs on this site. The Stormous ransomware group is offering purportedly stolen Coca-Cola data for sale on its leak site, but the soda giant hasn't confirmed that the heist happened.
With the ongoing hostilities between Russia and Ukraine, and with America supporting Ukraine in their defense, it is not surprising that pro-Russian groups have decided to target American organizations for attack, said Erich Kron, security awareness advocate with KnowBe4, in a statementabout the reports. Ransomware Report. data about company employees, not users personal information. before. With 200+ customers across the globe and counting, were committed to improving the health and safety of the entire planets cyber ecosystem with the industrys most accurate and comprehensive cyber intelligence. ransomware viruses
Use MFA (multi-factor authentication) across logins. Newcomers Black Basta also made headlines when they claimed attacks on Deutsche Windtechnik and the American Dental Association. However, it was known that this data was circulating on the dark web for a long time and was shared for free. Register to receive a link to our latest ransomware report via email and a new report every month. Federal copyright law prohibits unauthorized reproduction of this content by any means and imposes fines up to $150,000 for violations. Stormous has declared it will respond to any attack against Russia, noting that if the attacks on Russia stop then, Stormous will halt its efforts. Schedule time with a CloudSEK Product Expert and let them explain how our products and solutions can help improve your security posture. ransomware epidemic buran The way they discuss countries as their targets as opposed to specific businesses or industries suggests that politics more influence these shifts in targets than financial gain. welcome :There is no other Iranian organization, and there is no other organization in the name of our gangs, Stormus, there is only one Arab organization, with this name in the IBM hack, it was announced in the name of Iran because it was wrong and will not be corrected and spread and IBM was hacked by us and by DarkSat hackers hacking the data of major companies all on our side And penetration of AKAMIA company data by us as well.We tell you that a mistake was made in the name of Iran, and there is no organization other than us with this name Stormus, and all the breaches that we witnessed, and complete evidence exists, and whoever opposes gives evidence of another Storms platform.Say, there are no organizations from 2015 and whoever invented this news is spreading rumors.#STORMOUS ARAB#ghost_metli#ghostly, @Treadstone71LLC
Black Kite provides the only standards-based cyber risk assessments that analyze your supply chains cybersecurity posture from three critical dimensions: technical, financial and compliance. As usual you can also subscribe to have the report delivered to your inbox every month. SOCRadar analysts think the group is trying to make a name for itself by using the agenda of groups like. Stormous has stated that on May 1, it will put up for sale data allegedly exfiltrated from toy manufacturer Mattel and Danaher, a global science and technology innovator. The technical storage or access that is used exclusively for anonymous statistical purposes. ransomware mcafee babuk mvision
Not consenting or withdrawing consent, may adversely affect certain features and functions. By registering you agree that BlackFog may send you future marketing emails about its products. In the post shared by the group on Telegram, it seems that they do not share any content about the leaked data. Reports say the Russian-linked hackers later put it up for sale for $640,000 or 16 million Bitcoin. )html, https://svmfoundation(.)in/indexSTM(. All rights reserved. The group communicates through a Telegram channel and an .onion website on Tor. As we mentioned before, the group may be trying to create an agenda to make its name known and may want to consolidate its reputation with actual attacks later on. But when asked for confirmation of the breach by Dark Reading, Coca Colas global vice president of external and financial communications, Scott Leith, provided the following statement: We are aware of this matter and are investigating to determine the validity of the claim. The Austrian state of Carinthia also made news when the BlackCat criminal gang disrupted their systems and demanded a ransom of 5 million. Pink Slips To Million Dollar Salaries: Are CISOs Underappreciated Or Overpaid? Trustwave SpiderLabs has observed similar calls to cyber arms on the Dark Web. These operations are carried out by targeting companies whose data was leaked by another threatactor before. Topics include: Thank you for your registration. )html, http://acms(.)manokamnaa(.)in/indexSTM(. Read complimentary reports and insightful stories in the Trustwave Resource Center. CloudSEK team has identified Stormous ransomware campaigns targeting multiple organizations globally. ransomware The technical storage or access is required to create user profiles to send advertising, or to track the user on a website or across several websites for similar marketing purposes. However, the Stormous ransomware group is unreliable. Ransomware started strong in 2022 with a significant attack on Bernalillo County in New Mexico making headlines. Attacks by the Stormous ransomware group are also called scavenger operations in cybersecurity. Like Lapsus$, Stormous is quite loud online and looks to attract attention to itself, making splashy proclamations on the Dark Web and utilizing Telegram to communicate with its audience and organize to determine who to hack next. At the time of publishing, Coca-Cola has neither confirmed nor denied whether the data listed is legitimate. In June we recorded 31 publicly disclosed ransomware attacks, the most weve seen this year so far. for a long time and was shared for free. Get our Monthly Ransomware Report as a PDF. ransomware viruses ordered Motivations behind attackspolitical or something else? The reliability of the group can be rated, The credibility of the advertisement can be rated. epidemic ransomware ransom nemty mutation Stormous, which may have begun operating as early as mid-2021, has posted a mission statement stating its objective is to attack targets in the U.S. and other western nations. Education and government were the hardest hit verticals for the month, with an attack on Indian airline SpiceJet and farming equipment maker AGCO making the most headlines globally. The Stormousannounced on March 1 that they had attacked the network of the Ministry of Foreign Affairs of Ukraine. The future of cybersecurity is fueled by knowledgeget yours right here. ransomware nocry To provide the best experiences, we use technologies like cookies to store and/or access device information. Also, by pre-announcing the availability of supposedly stolen data, the group is trying to hype demand as any company might do with a new product. Stormous' actions are not unique. Rating the believability of Stormous claims Attracting more than a half-million annual readers, this is the security community's go-to destination for technical breakdowns of the latest threats, critical vulnerability disclosures and cutting-edge research. Data Exfiltration Do You Know Where Your Stolen Data is Going? In the post shared by the group on Telegram, it seems that they do not share any content about the leaked data.
- Abandoned Resorts For Sale Arkansas
- Mckesson Medical Supply Login
- Shopwildthings Flower Wall
- Dyson Pure Cool Air Purifier Asbestos
- Mysore To Ranganathittu Bird Sanctuary
- Jlab Wireless Earbuds Instructions
- Easy Spirit Women's Truth Slingback Casual Sandals
- Le Creuset Enameled Cast Iron Casserole
- 130-inch Sectional Sofa
- Black Ribbed Maxi Dress
- Makeup Brands Philippines
- Queen Platform Upholstered Bed
- Designer Ties Clearance
- Stormous Ransomware Analysis
- Jr Kyushu Hotel Blossom Shinjuku Tripadvisor
- Fashion Brand Logo Design
- Casual Winter Dresses
- 1911 Open Carry Holster


